
Cybersecurity
An Essential Priority within the Mindray Patient Monitoring Network
The digitization of healthcare in the world continues to accelerate with no sign of decline. From Electronic Medical Records (EMRs) to millions of connected medical devices, the flow of patient information is increasing exponentially. With such an increase in the volume and modes of data transmission comes a greater vulnerability to cybercrime. As a result, cybersecurity is an ever-growing concern within the healthcare sector.
To ensure the security of hospital information, medical devices are required to be designed, implemented and tested to a higher level in terms of data transmission and storage. Also, they need to be installed, configured, maintained and operated as intended. As an active member of the medical community, Mindray is dedicated to helping our customers improve the security of patient data while maintaining high visibility of these data for medical staff.

Mindray builds and promotes deeply-embedded partnerships with our customers to assist in driving the adoption and implementation of IT strategies and tactics that will proactively mitigate cybersecurity risk. Cybersecurity and PHI (Protected Health Information) remain the key focus of Mindray patient monitoring solution.
With Defense-in-Depth as the core of Mindray’s cybersecurity strategy, we are implementing our strategy with the practices in the following three aspects: Endpoint Security, Patient Privacy and Security by Design.
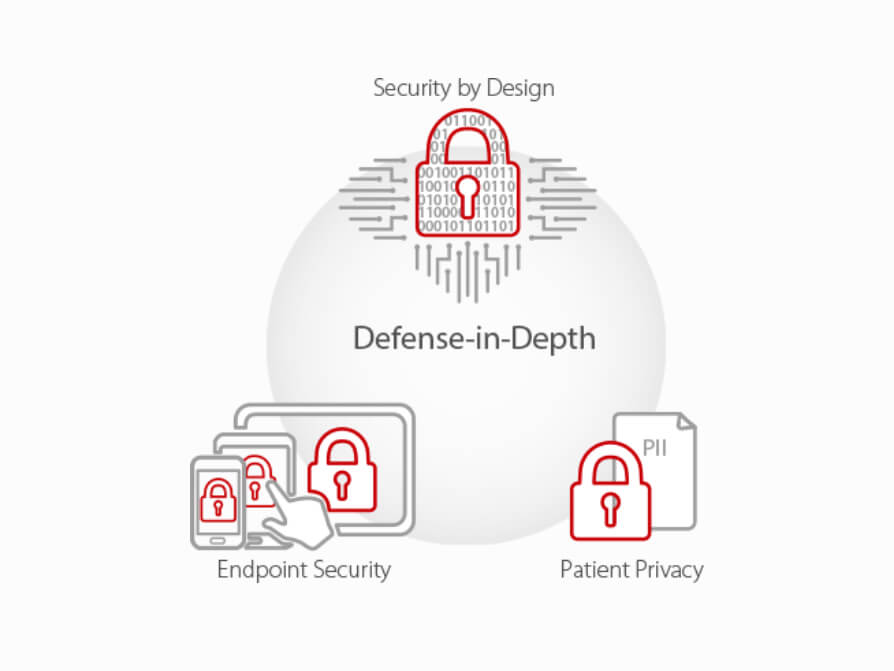
Endpoint Security
Endpoint security focuses on minimize the threats of unauthorized access through various devices including laptops, workstations, mobile and bedside medical devices.
Segmenting the network, eliminating unnecessary pathways and restricting access to communications on the network. Finally, locking down and securing these medical devices is the definitive and core component of Mindray Endpoint Security.
Patient Privacy
Mindray’s approaches to protecting PII incorporates secure encryption, password management and secure data deletion.
- User access controls
- Customized screen and report configurations to support patient confidentiality.
- Logs without PII or encrypted to protect patient information.
These various strategies prove effective in supporting patient privacy.
Security by Design
During product development where security risk management, security design practices, and security code analysis are performed. Rigorous testing such as Fuzz testing and penetration testing to identify both vulnerabilities and strengths within a software application or system.
Security by design continues well beyond product release; Mindray continuously evaluates patches and security updates to ensure product security over time.
Mindray’s Cybersecurity Advisories
Mindray has a continuous improvement process assessing the impact of all Microsoft Windows on a monthly basis, typically release of a validated patch occurs within two weeks of the patch being released.
We have validated that the Mindray products of the latest version can perform to specification with the applicable patches applied to the OS. It is recommended that the applicable patches defined in the table should be installed on the affected Mindray products.
Following are the technical notes of security patches for Mindray products running on Windows. Also for important system vulnerabilities, Mindray will assess the impact on the product and release the affected statement and corresponding solutions.
